The word “cybersecurity” inspires images of ransomware attacks or phishing emails targeting internal staff.
But what about the vendors you work with every day?

Medical billing partners routinely access sensitive patient data, and if their cybersecurity defenses are weak, your reputation and compliance can be on the line.
Hospitals and ASCs are increasingly being held accountable for the cybersecurity of their vendors. So, what can you do to protect your patients and your organization?
We spoke with JD Keith, CSI IT and Cybersecurity Lead, to learn more about cybersecurity, patient data security, and choosing a dependable medical billing partner.
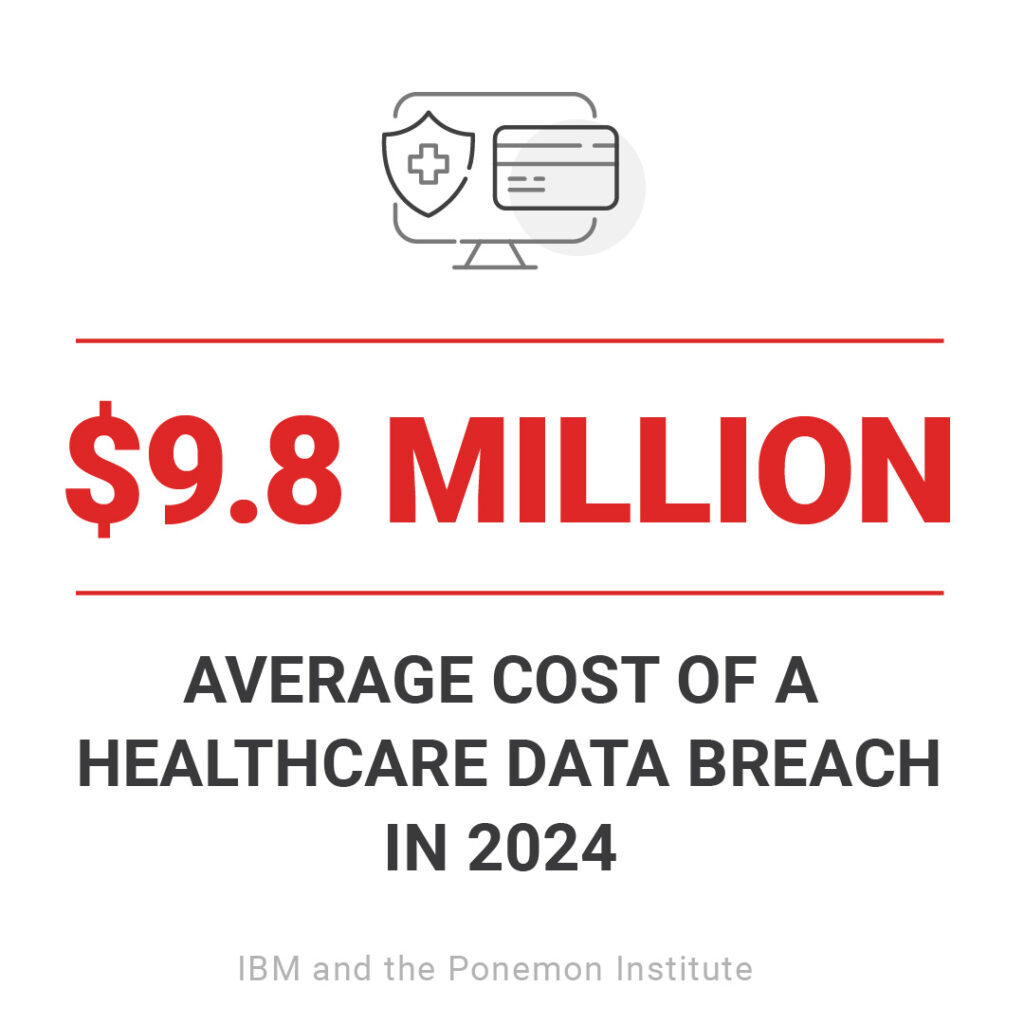
Breaches Are Inevitable
Healthcare remains one of the top targets for cybercrime. Threat actors exploit any point of access: hospitals, outpatient centers, and increasingly, third-party billing and DME vendors.
“It’s not if you get hacked, it’s when. The goal isn’t to be invincible. It’s to be prepared, minimize impact, and bounce back fast.” – JD Keith, CSI IT and Cybersecurity Lead
CSI’s cybersecurity protocols are designed with this reality in mind. “We monitor all avenues of attack vectors—internal, external, and everything in between,” Keith explains. “You have to be watching all the time.”
By applying principles such as least privilege and system isolation, CSI limits the scope of potential breaches. Each user is granted only the access required to perform their role—nothing more.
Why This Matters for Providers
More than ever before, hospitals and ASCs are being held accountable for the cybersecurity practices of their vendors. “You are responsible for your third-party vendors,” Keith emphasizes. “Understanding and documenting their security posture is all part of due diligence.”
Numerous legal precedents affirm this shared liability. In New Jersey, one medical group paid $418,000 after a vendor’s misconfiguration exposed patient data. Another in New York faced a $550,000 fine related to delayed patching by a third-party partner. In each case, the provider bore the consequences—even when the fault lay with an external entity.
Choosing a secure billing partner is no longer optional. It is an integral part of HIPAA compliance, risk management, and institutional trust.
What Sets CSI Apart
CSI integrates cybersecurity into daily operations. The approach blends technical safeguards with human awareness.
- 24/7 Monitoring: Internal and external threat activity is continuously assessed.
- Secure Access: Multi-factor authentication (2FA), biometric login, and separate admin/user accounts are standard.
- Proactive Culture: Regular quarterly training helps all staff members recognize phishing attempts and suspicious activity.
- No Shortcuts: Shared logins are prohibited; password rotations are enforced; access logs are documented in detail.
Keith explains that ASCs and hospitals should be asking “the hard questions” about all of these security measures with potential vendors. How is access managed? What proves compliance? What safeguards are in place to detect and contain future threats?
Providers should compare cybersecurity practices to their own to ensure that a vendor can uphold the required level of patient data security.

Proof Over Promises
Many vendors claim to take cybersecurity seriously. CSI backs that claim with measurable practices and external benchmarks:
- Industry Standards: CSI adheres to frameworks such as NIST, tailored for healthcare environments. While sensitive certifications are not shared publicly, documentation and internal protocols are available to clients upon request.
- Medical Device Compliance: As an FDA Class II medical device company, CSI tracks every product and access point to maintain the highest standard.
“We’re not just here to handle billing, we’re here to protect your patients’ data like it was our own.” J.D. Keith
A Partnership Based On Patient Data Security
In today’s healthcare landscape, trust is not assumed. It is verified.
For any healthcare provider seeking clarity and confidence in their medical billing partnerships, CSI is ready to engage.
Ready for a deeper conversation about patient data security? Let’s talk.
